This was one of the most interesting attacks showed on Black Hat Las Vegas 2015. Let’s imagine the situation: there’s a large park of Windows computers in a large organization, and they all need to be updated. Obviously, getting all of them to download updates over the Internet is both pricy and uncomfortable. The common solution is a WSUS (Windows Server Update Services) server, which is used to manage updates. It downloads the updates and delivers them to all other computers.
This is a typical task and the solution is standard, so WSUS is widely adopted. This also makes it an attractive target for attacks. The Contextis company examined the principles of its work and developed an attack, which is both very powerful (you can get RCE with System privileges) and easy to reproduce. The white paper is voluminous, so we’ll concentrate on the main points.
So the company has a WSUS server, and the end hosts are configured through group policies to address this particular server for the updates. They use SOAP protocol, which by default works over HTTP. This is one of the most important factors for us. The standard port is 8530.
You can find a path to the end host in this registry node.
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate\WUServerHere’s how the interaction between different hosts works. First of all the end host registers itself on the server and gets a cookie in reply, which is used later to access the server. After that the host routinely (usually once in 24 hours) requests if there’s an update. WSUS responds with a list of updates and paths, which can be used to download an update (also on WSUS). In case of an automated update the host downloads and installs the data found in the update (from SYSTEM, of course). There’s a similar process for installing drivers. In fact this process (and also the protocol) is identical to updating through Windows Update.
Only those updates can be installed that are signed with a valid Microsoft certificate. It is the primary component of the defence.
Several types of updates were found during the research. The most interesting for us is CommandLineInstallation (it’s a handler from the query). It uploads an executable file to the OS and runs it with particular parameters (for example this is used to run Microsoft’s antivirus).
So we have some hosts and a WSUS server. They communicate over an unprotected HTTP, so we can execute a MitM attack to change the data in the SOAP requests and the responses (SOAP requests themselves are not signed). The client has no means to check if the updates are real, we can install whatever we want during the attack. Using CommandLineInstallation we can execute any commands with any parameters in the OS.
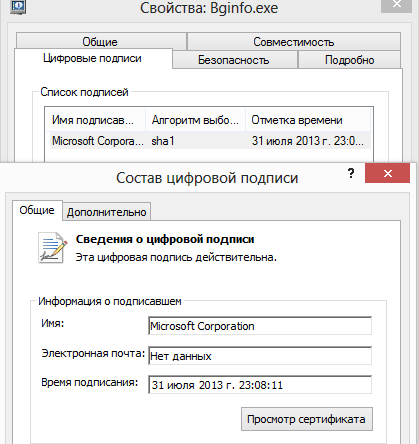
Of course the executable file must be signed with a Microsoft certificate, but there’s no special Windows Update certificate. We can use any of them. Contextis suggests Mark Russinovich’s Sysinternals Tools as an excellent option. Since these tools were officially adopted by Microsoft they have a valid signature. With PsExec we can execute any commands and run any software (Meterpreter for example). We can also use BGinfo, since some third party antiviruses do not like PsExec.
As we can see, with default settings the system is extremely vulnerable. The main problem boils down to making the end host request updates from WSUS, so that we wouldn’t have to wait for 24 hours to execute an attack.

2022.06.01 — F#ck AMSI! How to bypass Antimalware Scan Interface and infect Windows
Is the phrase "This script contains malicious content and has been blocked by your antivirus software" familiar to you? It's generated by Antimalware Scan Interface…
Full article →
2023.02.21 — SIGMAlarity jump. How to use Sigma rules in Timesketch
Information security specialists use multiple tools to detect and track system events. In 2016, a new utility called Sigma appeared in their arsenal. Its numerous functions will…
Full article →
2022.01.12 — First contact. Attacks against contactless cards
Contactless payment cards are very convenient: you just tap the terminal with your card, and a few seconds later, your phone rings indicating that…
Full article →
2023.06.08 — Cold boot attack. Dumping RAM with a USB flash drive
Even if you take efforts to protect the safety of your data, don't attach sheets with passwords to the monitor, encrypt your hard drive, and always lock your…
Full article →
2022.02.15 — Reverse shell of 237 bytes. How to reduce the executable file using Linux hacks
Once I was asked: is it possible to write a reverse shell some 200 bytes in size? This shell should perform the following functions: change its name…
Full article →
2022.04.04 — Fastest shot. Optimizing Blind SQL injection
Being employed with BI.ZONE, I have to exploit Blind SQL injection vulnerabilities on a regular basis. In fact, I encounter Blind-based cases even more frequently…
Full article →
2022.06.01 — WinAFL in practice. Using fuzzer to identify security holes in software
WinAFL is a fork of the renowned AFL fuzzer developed to fuzz closed-source programs on Windows systems. All aspects of WinAFL operation are described in the official documentation,…
Full article →
2022.06.03 — Challenge the Keemaker! How to bypass antiviruses and inject shellcode into KeePass memory
Recently, I was involved with a challenging pentesting project. Using the KeeThief utility from GhostPack, I tried to extract the master password for the open-source KeePass database…
Full article →
2023.04.19 — Kung fu enumeration. Data collection in attacked systems
In penetration testing, there's a world of difference between reconnaissance (recon) and data collection (enum). Recon involves passive actions; while enum, active ones. During recon,…
Full article →
2022.01.13 — Step by Step. Automating multistep attacks in Burp Suite
When you attack a web app, you sometimes have to perform a certain sequence of actions multiple times (e.g. brute-force a password or the second authentication factor, repeatedly…
Full article →